From charlesreid1
Normally when capturing traffic with tcpdump, it puts the network interface into promiscuous mode.When not running in promiscuous mode, the NIC only receives frames destined for its own MAC address as well as broadcast and multicast addresses.
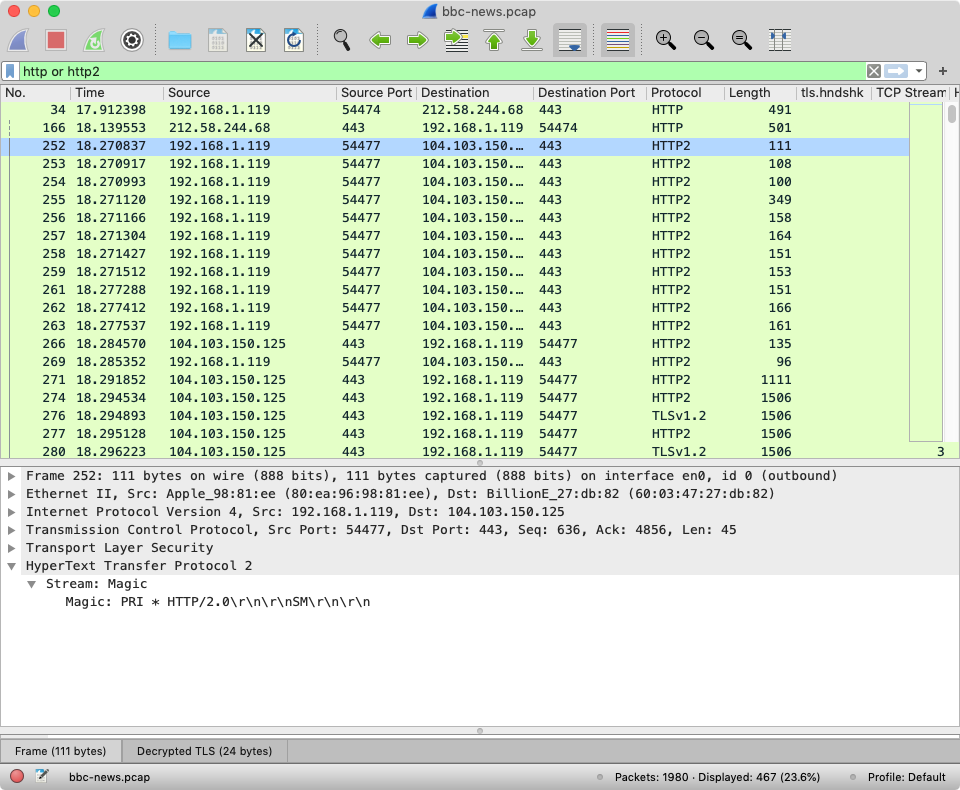
- Find FTP Traffic. Find Cleartext Passwords. Find Packets With Evil Bit. Install tcpdump with apt install tcpdump (Ubuntu), or yum install tcpdump (Redhat/Centos) Let’s start with a basic command that will get us HTTPS traffic: tcpdump -nnSX port 443.
- You can easily install tcpdump using the package manager of your distro. Installing tcpdump on Ubuntu and Debian # sudo apt update && sudo apt install tcpdump.
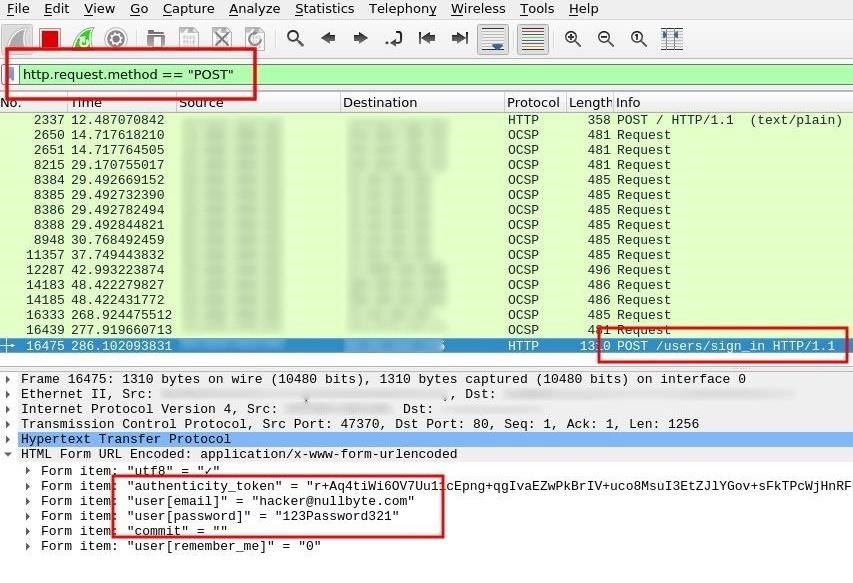
- 1Installing
- 2Basic Usage
- 2.2Controlling Output
- 4More Flags
- 5Analysis
Linux
tcpdump should come with your distro, but if it doesn't, use aptitude or your package manager to install:
Once you've done that, you can list your network devices:
Pick out which ones you want to listen to.
Mac
tcpdump comes with Mac. Man page for tcpdump: https://developer.apple.com/library/mac/documentation/Darwin/Reference/ManPages/man1/tcpdump.1.html
List your network devices:
Pick out which ones you want to listen to.
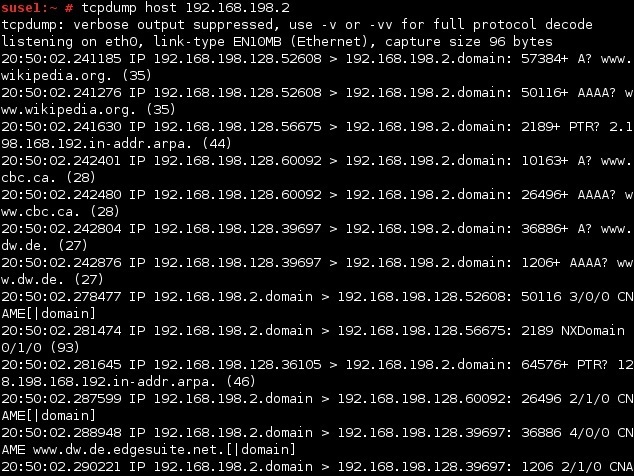
You may need to run tcpdump as sudo to access certain information from the hardware.
Tcpdump options can vary from platform to platform (e.g. mac vs linux) but this guide will cover some universal usage.
Tcpdump Mac Address
The simplest way to use tcpdump is to do an unfiltered packet capture - no filters on packets, so everything is captured.
The bare minimum you'll have to specify is a network interface. You may want to specify a file, too.
The -i and -w flags
To specify a network device you want to listen to, use the -i flag (for interface). Also specify an output file with the -w flag:
-w prevents your computer from having a meltdown trying to print every single packet in a busy place.
You can monitor multiple interfaces by specifying a list: -i en0,en1
If you are using wireless, you'll need to use additional commands to control the channel your wireless card is listening to.
Controlling Output
To control output, you can have tcpdump create a new pcap file every N seconds, or every N megabytes.
G flag
Use the G flag to create a new pcap file every N seconds:
If you use the G flag without the C flag (see below), you specify new filenames with strftime date/time format when you pass the filename to the -w flag.
This command makes a new pcap file every 100 seconds:
C flag
The C flag sets the maximum pcap file size, in millions of bytes. New files will have a common name with an incrementing number at the end. From the man page:
W flag
The W flag will limit the number of output files, so that tcpdump will begin to overwrite the first file once it has finished writing to the Nth file:
More instructions on capturing wireless packets with Tcpdump: Tcpdump/Wireless
Faster Packet Capture
To minimize overhead processing packets and maximize the number of packets captured, you can turn off host name resolution with the -n flag. This also makes things slightly more readable.
Writing Packets To File
If you want to force tcpdump to write every packet to the output file as it is received, rather than waiting until its input buffer is full, you can use the U flag. Note that this will be slower and should only be done when traffic is light - otherwise excessive disk writes will bog things down.
From the man page:
You can also use tcpdump to analyze a pcap file.
Reading Packets
To read packet data, run tcpdump with the -r flag (for read):
Counting Packets
Not sure if this will work:
This will give you a count of the total number of packets in the pcap file.
Parsing Information
You can parse information by column using the cut utility.
The output has the fields:
Introduction
In this tutorial, we’re going to bring you a popular network tool you should know about in order to correctly manage your networks.
We are assuming that you have root permission, otherwise, you may start commands with “sudo”.
Install TCPdump
How To Install Tcpdump For Mac High Sierra
TCPdump is a powerful command-line packet analyzer tool which used to capture or filter TCP/IP packets that received or transferred over a network on a specific interface. it’s available on every Linux flavor for free of course.
Install TCPdump on CentOS:
Install TCPdump on Debian and Ubuntu:
Once the TCPdump tool is installed, you can continue to browse following commands.
Capture packets from a specific interface
If you execute the TCPdump command with the “-i” flag you can name an interface and the TCPdump tool will start capture that specific interface packets for you.
Capture only specific number of packets
Using “-c” flag will allow you to capture a specific number of packets, for example, with the command below we can capture 20 packets of our eth0 interface:
Print captured packets in ASCII
The below TCPdump command with the flag “-A” displays the packages in ASCII format. it’s a character-encoding scheme format.
Display available interfaces
To get a list of available interfaces on the system you can run the following command:
Capture and save packets in a file
TCPdump has a feature to capture and save its result in a “.pcap” file, to do this just execute:
If you don’t use “-c” flag it will start capturing eth0 and write the result to the output file until you break it with “Ctrl+c”.
For read and analyze the file that you just created execute:
Capture IP address packets
If you want to capture your network interface and analyze the IP address you can use the “-n” flag it will stop translating IP addresses into Hostnames and This can be used to avoid DNS lookups.
Capture only TCP packets
To capture packets based on TCP ports, add a “tcp” in your command:
Capture packets from a specific port
Let’s assume you want to monitor on a specific port like 80, you can use the following command to do that with TCPdump:
Filter records with source and destination IP
To Capture packets from a source IP you can use the following command:
You can monitor packets from a destination IP as well with the command below:
You can find more information about TCPdump on its official website!